Cryptographic algorithms
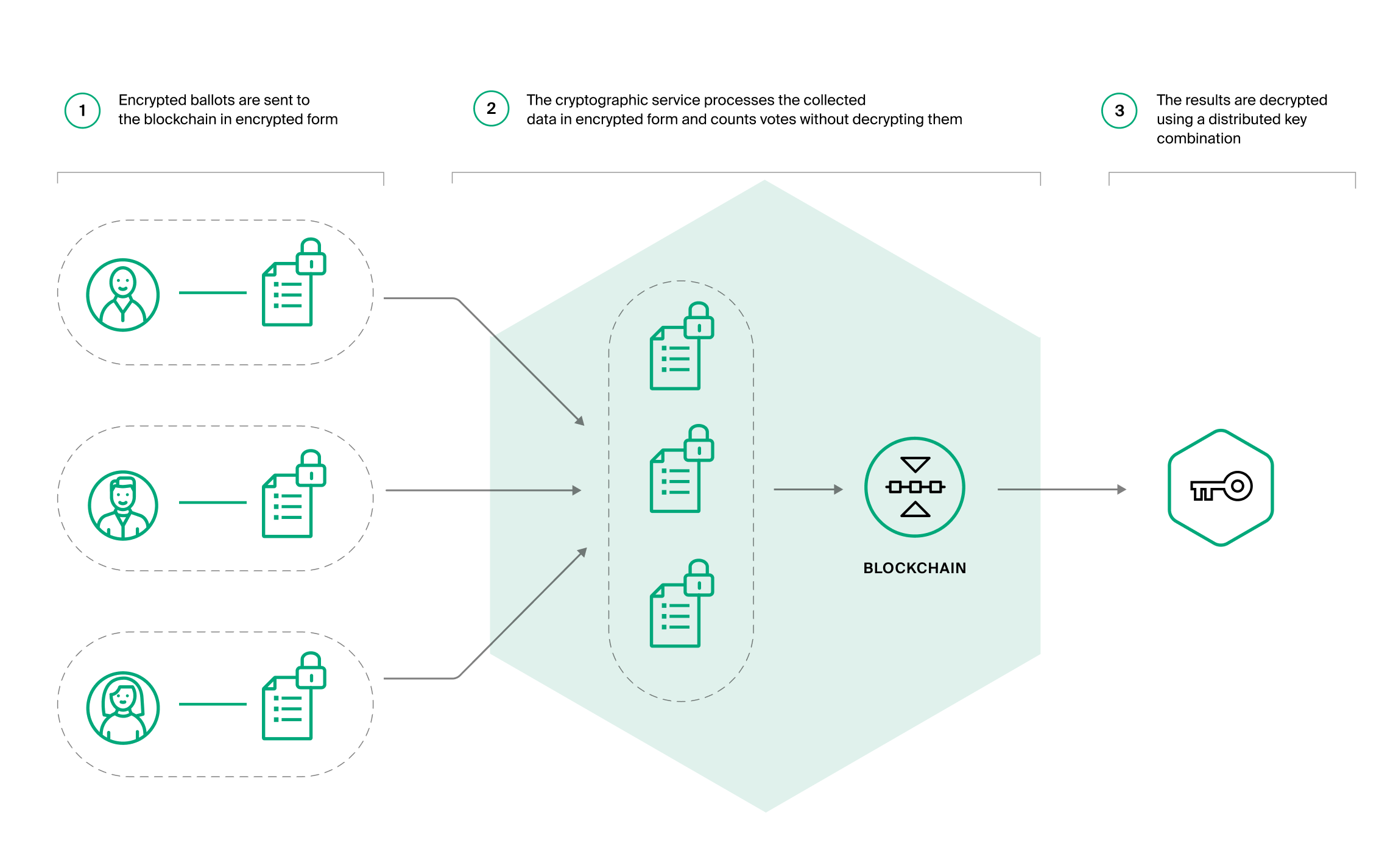
All WE.Vote polls are well protected with cryptographic algorithms, which provide poll and ballot data encryption. There is no need to decrypt data in order to prove both validity and relevance.
All the stages of voting in WE.Vote use cryptographic algorithms. A vote is encrypted right on the voter’s device and sent to the service in encrypted form. The cryptographic protocol preserves ballot secrecy while processing and tallying of votes is taking place. At the end, results are decrypted and provided to the poll administrator.
You can find more information about WE.Vote cryptographic algorithms, including DKG Pedersen 91 and the El Gamal cryptosystem based on elliptic curves and zero-knowledge proofs, in our service documentation.
other products page works